Overview
Default permissions define the base-level access control for each canonical object (entity type) in your Entegrata Lakehouse. These permissions apply to all resources of a specific entity type unless overridden by more specific access rules. Understanding and properly configuring default permissions is crucial for establishing a secure foundation for your data access control.How Default Permissions Work
Default permissions operate at the entity level and provide a baseline for access control:- Entity-Level Application: Each canonical object type (e.g., Client, Matter, Timekeeper) has its own default permission setting
- Global Scope: Default permissions apply to all resources within an entity type across your entire instance
- Override Capability: Specific access rules can override default permissions for targeted subjects and resources
- Permission Inheritance: New resources automatically inherit the default permissions of their entity type
Default permissions are the starting point for access control. They should be set based on your organization’s general access philosophy - either “default open” (allow by default) or “default closed” (deny by default).
Access Requirements
To configure default permissions, you must have:- Administrative privileges in the Entegrata Admin Portal
- Access to the Data Mapping configuration
- At least one mapped entity in your system
- Understanding of your organization’s data access policies
Configuring Default Permissions
Step 1: Navigate to Entity Access Control
- Go to Data → Mapping in the main navigation
- Select the mapping configuration you want to modify
- Click on the specific entity you want to configure
- Navigate to the Access Control tab

Step 2: View Current Default Permissions
The Access Control tab displays a card showing the current default permission setting: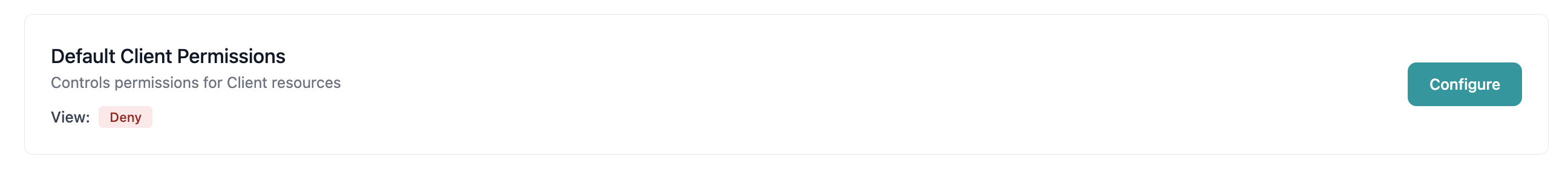
The permission level for viewing resources of this entity type. Can be set to:
- Allow: All users can view resources by default
- Deny: No users can view resources by default (requires explicit rules to grant access)
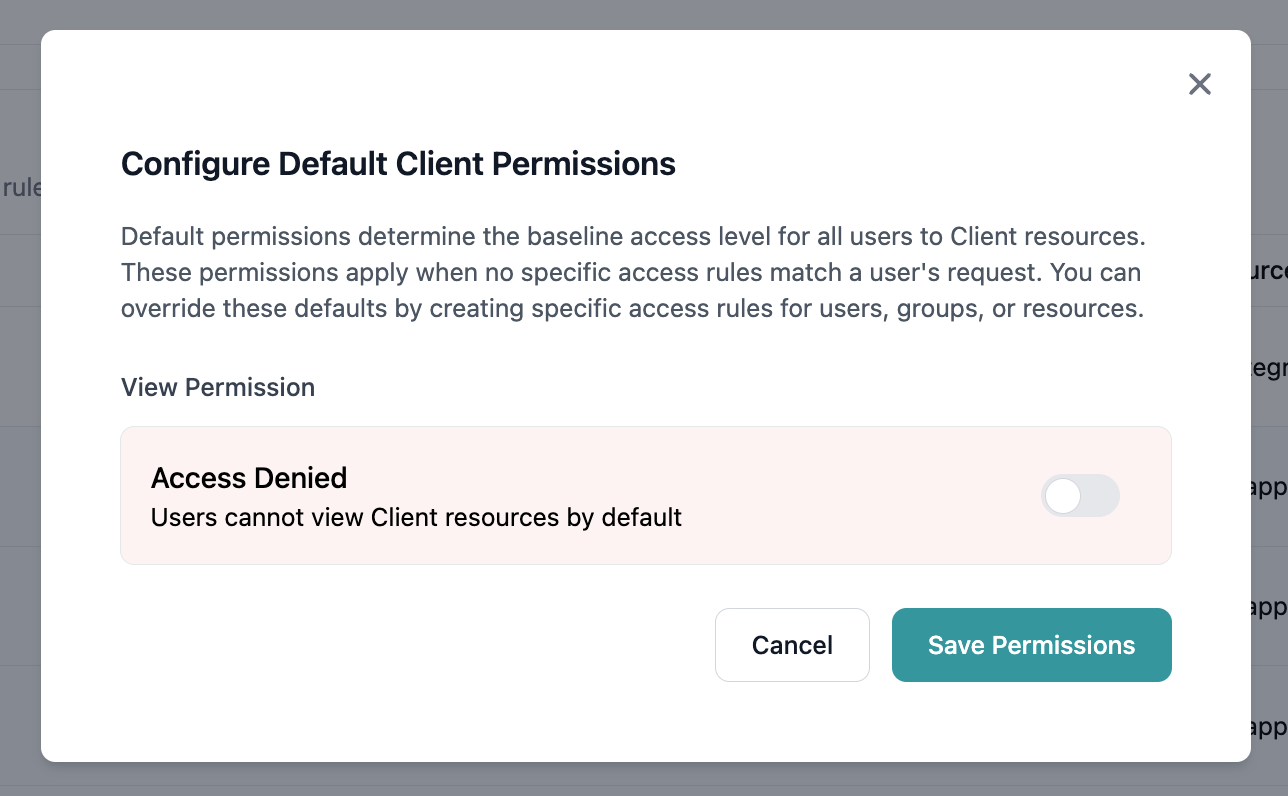
Step 3: Modify Default Permissions
- Click the Configure button on the Default Permissions card
- The configuration modal will open
-
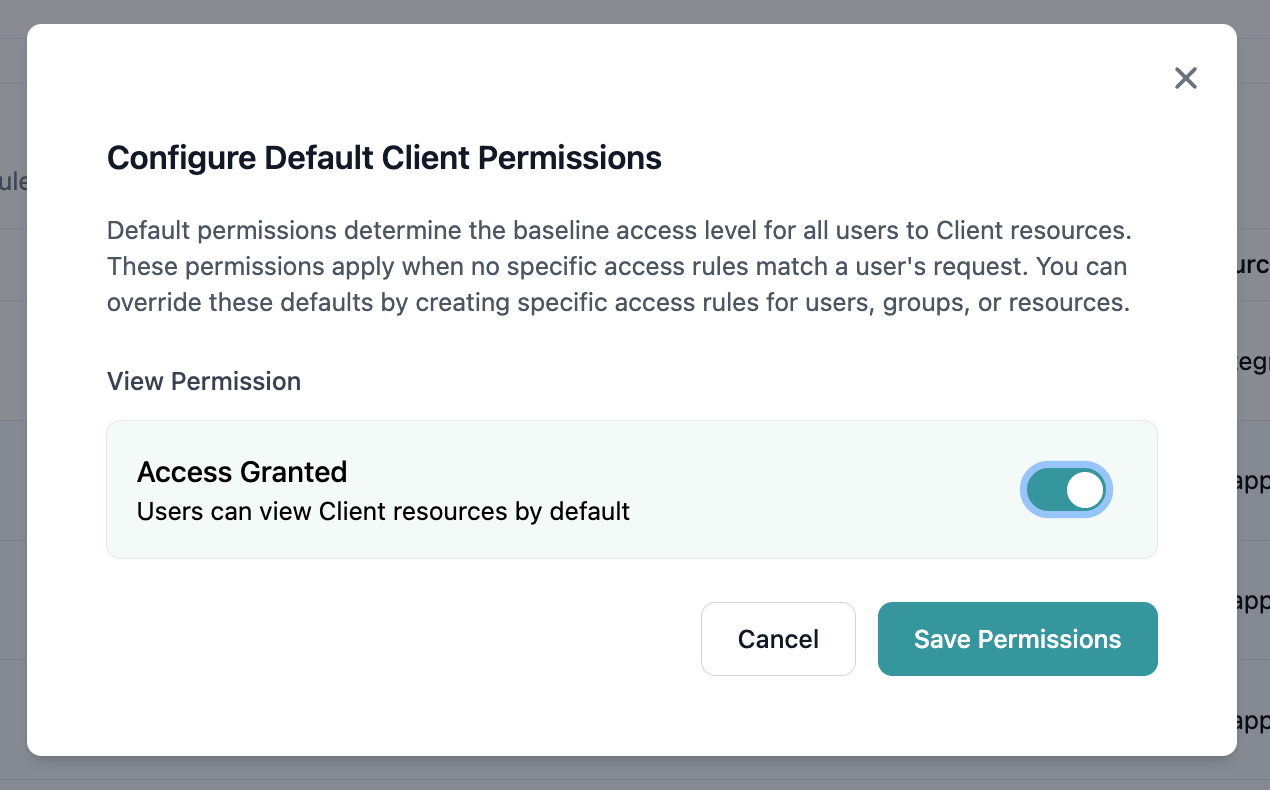
Toggle the permission setting:
- Enable (Green) = Allow access by default
- Disable (Red) = Deny access by default
- Review the impact statement that explains how this setting affects access
- Click Save to apply the changes
Step 4: Verify Changes
After saving:- The default permissions card will update to reflect the new setting
- The permission badge will show the current state (green for Allow, red for Deny)
- The change is logged in the audit trail with timestamp and user information
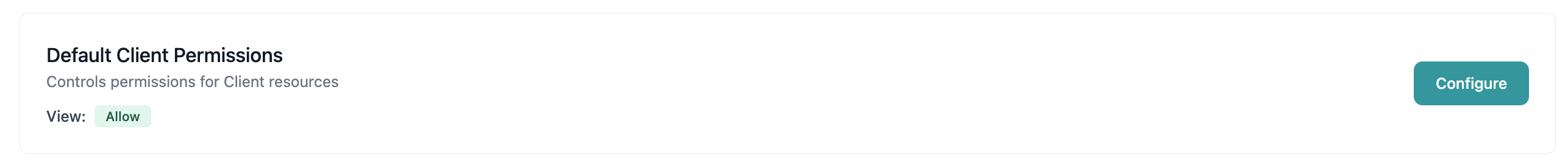
Permission Precedence
Understanding how default permissions interact with specific rules is crucial:Default Permission Applied
When a user attempts to access a resource, the system first checks the default permission for that entity type
Rule Evaluation
The system then evaluates any specific rules that apply to the user (directly or through groups) and the resource
Most Specific Wins
More specific rules override default permissions. A rule targeting a specific user and resource takes precedence over entity-level defaults
Best Practices
Choosing Your Default Strategy
- Default Deny (Recommended)
- Default Allow (Not Recommended)
When to use:
- Always for law firms and legal data
- Sensitive or regulated data
- Compliance requirements
- Production environments with strict security
- Maximum security by default
- No accidental data exposure
- Explicit grants required for all access
- Clear audit trail of permissions
- Meets compliance requirements
- Set all canonical objects to Deny by default
- Create explicit rules for necessary access
- Use groups to manage access efficiently
- Document all permission grants
Configuration Guidelines
Common Scenarios
Scenario 1: Public Reference Data
For entity types containing non-sensitive reference data (e.g., office locations, practice areas):- Set default permission to Allow
- No additional rules needed for basic access
- Add deny rules only for specific exceptions
Scenario 2: Client Confidential Data
For entity types containing sensitive client information:- Set default permission to Deny
- Create rules to grant access to authorized teams
- Use group-based rules for easier management
Scenario 3: Mixed Sensitivity Data
For entity types with varying sensitivity levels:- Set default permission based on the most common case
- Use rules to handle exceptions
- Consider splitting into multiple entity types if complexity grows
Impact on Other Features
Default permissions affect several aspects of the system:- Data Discovery: Users can only discover resources they have permission to view
- Reporting: Reports only include data the user has permission to access
- API Access: API calls respect default permissions and rules
- Search Results: Search returns only permitted resources
Troubleshooting
Users Can’t Access Expected Data
- Check the default permission for the entity type
- Verify no deny rules are blocking access
- Test permissions using the testing tools
- Review group memberships if using group-based rules
Users Have Unexpected Access
- Review default permissions (may be set to Allow)
- Check for overly broad allow rules
- Audit group memberships
- Use permission explorer to trace access path
Changes Not Taking Effect
- Allow 1-2 minutes for propagation
- Clear user session cache if immediate update needed
- Verify the change was saved successfully
- Check for conflicting rules that might override defaults
Related Topics
- Creating Access Rules - Override defaults with specific rules
- Testing Permissions - Verify your configuration
- Managing Groups - Organize users for rule application
- Enabling Access Control - Initial setup steps
