Overview
Firewall rules control which external services and resources your Entegrata instance can communicate with. By defining application rules (for domain names) and network rules (for IP addresses), you establish granular control over your instance’s outbound network access. This is a critical security feature that:- Restricts outbound connections to only approved destinations
- Prevents unauthorized data exfiltration
- Ensures compliance with security policies
- Enables safe communication with data sources and third-party services
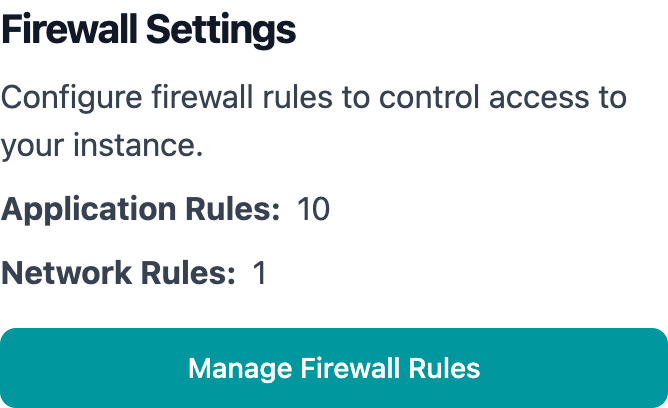
Firewall rules complement your network connection settings (S2S VPN or VNet Peering) by controlling what your Entegrata instance can access once connected to your infrastructure.
Understanding Firewall Rules
Rule Categories
Entegrata organizes firewall rules into two distinct categories:Collector Rules
Collector Rules
Purpose: Data sources and systems accessed by Entegrata collectorsCharacteristics:
- Created automatically when collectors are configured
- Can be viewed and managed by administrators
- Represent actual data collection endpoints
api.salesforce.com- Salesforce API accessgraph.microsoft.com- Microsoft Graph API192.168.1.50- On-premises database server
Collector rules are typically generated by the collector configuration process but can be manually adjusted if needed.
Custom Rules
Custom Rules
Purpose: User-defined rules for specific business requirementsCharacteristics:
- Fully customizable by administrators
- Can be added, edited, and deleted as needed
- Used for special integrations or custom data sources
*.customapi.company.com- Internal API endpoints203.0.113.100- Third-party service IPwebhook.service.io- External webhook destinations
Rule Types
Firewall rules come in two types, each serving different networking scenarios:- Application Rules (FQDN)
- Network Rules (IP/CIDR)
What they are: Domain-based rules that match Fully Qualified Domain Names (FQDNs)Use cases:
- Cloud APIs (e.g.,
api.example.com) - SaaS platforms (e.g.,
app.salesforce.com) - Services with dynamic IPs
- CDN-backed services
- Exact domains:
api.example.com - Wildcard subdomains:
*.example.com - Multiple domain levels:
app.subdomain.example.com
- Works with cloud services that use dynamic IPs
- Clearer, more readable than IP addresses
- Automatically adapts to IP changes
Understanding the Rules Display
Each firewall rule displays the following information:The FQDN or IP address that the rule applies to.Examples:
api.salesforce.com(Application rule)192.168.1.100(Network rule)*.azure.com(Wildcard application rule)
Indicates whether the rule is an Application (FQDN) or Network (IP/CIDR) rule.
Shows if the rule is Collector or Custom.
For Collector and Custom rules, edit and delete actions are available.
Adding New Firewall Rules
Create a New Rule
Open Add Rule Dialog
In the firewall management interface, click the Add Rule button in the Collector or Custom section.

Select Rule Type
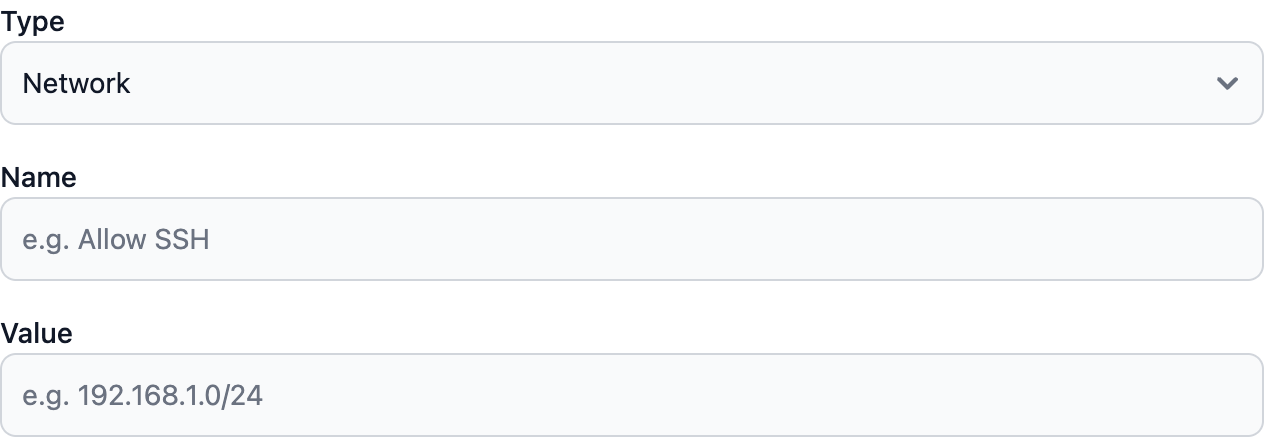
Choose between Application Rule (FQDN) or Network Rule (IP/CIDR) based on your needs.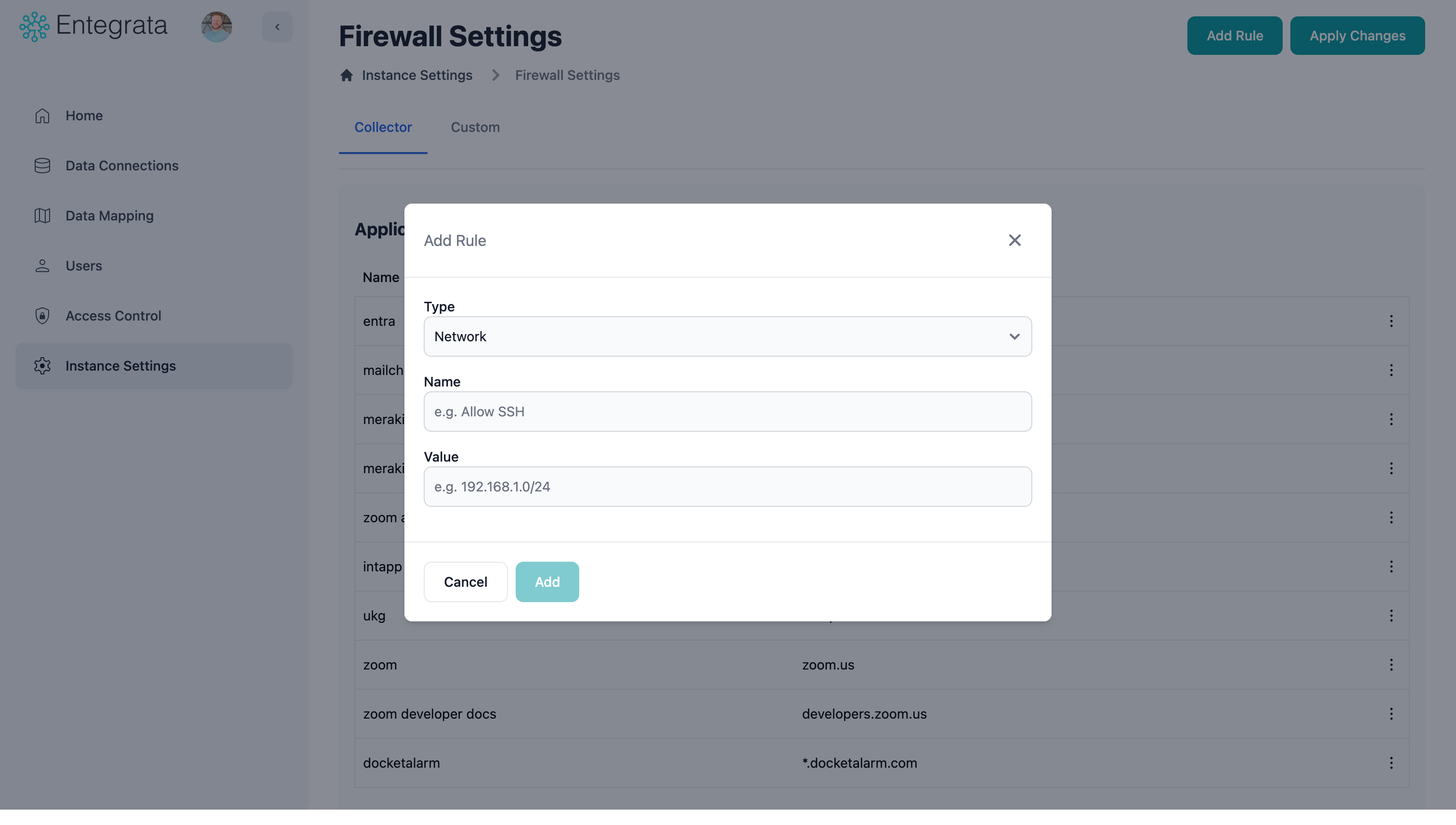

- For Cloud Services
- For IP-Based Systems
Select Application Rule if you’re adding access to:
- Cloud APIs with domain names
- SaaS platforms
- Services with dynamic IPs
Enter Rule Details
Fill in the required information based on your rule type.
- Application Rule
- Network Rule
FQDN (Domain Name)Enter the fully qualified domain name:
- Exact match:
api.example.com - Wildcard subdomain:
*.example.com
- Domain length: 3-255 characters
- Each label (part between dots): max 63 characters
- Must have valid top-level domain (TLD)
- Supports single wildcard at beginning (
*.)

Choose Rule Category
Select whether this rule should be categorized as Collector or Custom.Collector: For data sources accessed by collectors Custom: For other integrations and services
Validation Examples
Valid FQDN Examples
Valid FQDN Examples
✅ These will be accepted:
api.salesforce.com*.azure.comapp.subdomain.example.comservice-123.cloud.provider.netmy-api.example.co.uk
Invalid FQDN Examples
Invalid FQDN Examples
❌ These will be rejected:
*.com(wildcard too broad)example(missing TLD)http://api.example.com(includes protocol)api.example.com:443(includes port)api..example.com(double dots)
Valid IP/CIDR Examples
Valid IP/CIDR Examples
✅ These will be accepted:
192.168.1.100192.168.1.100/3210.0.0.0/24172.16.0.0/16203.0.113.0/28
Invalid IP/CIDR Examples
Invalid IP/CIDR Examples
❌ These will be rejected:
256.1.1.1(octet > 255)192.168.1.1/33(CIDR > 32)192.168.1(incomplete IP)2001:db8::1(IPv6 not supported)192.168.1.1-192.168.1.10(range notation not supported)
Editing Existing Rules
Modify a Rule
Modify Rule Details
Update the FQDN, IP address, or CIDR range as needed.The same validation rules apply as when creating a new rule.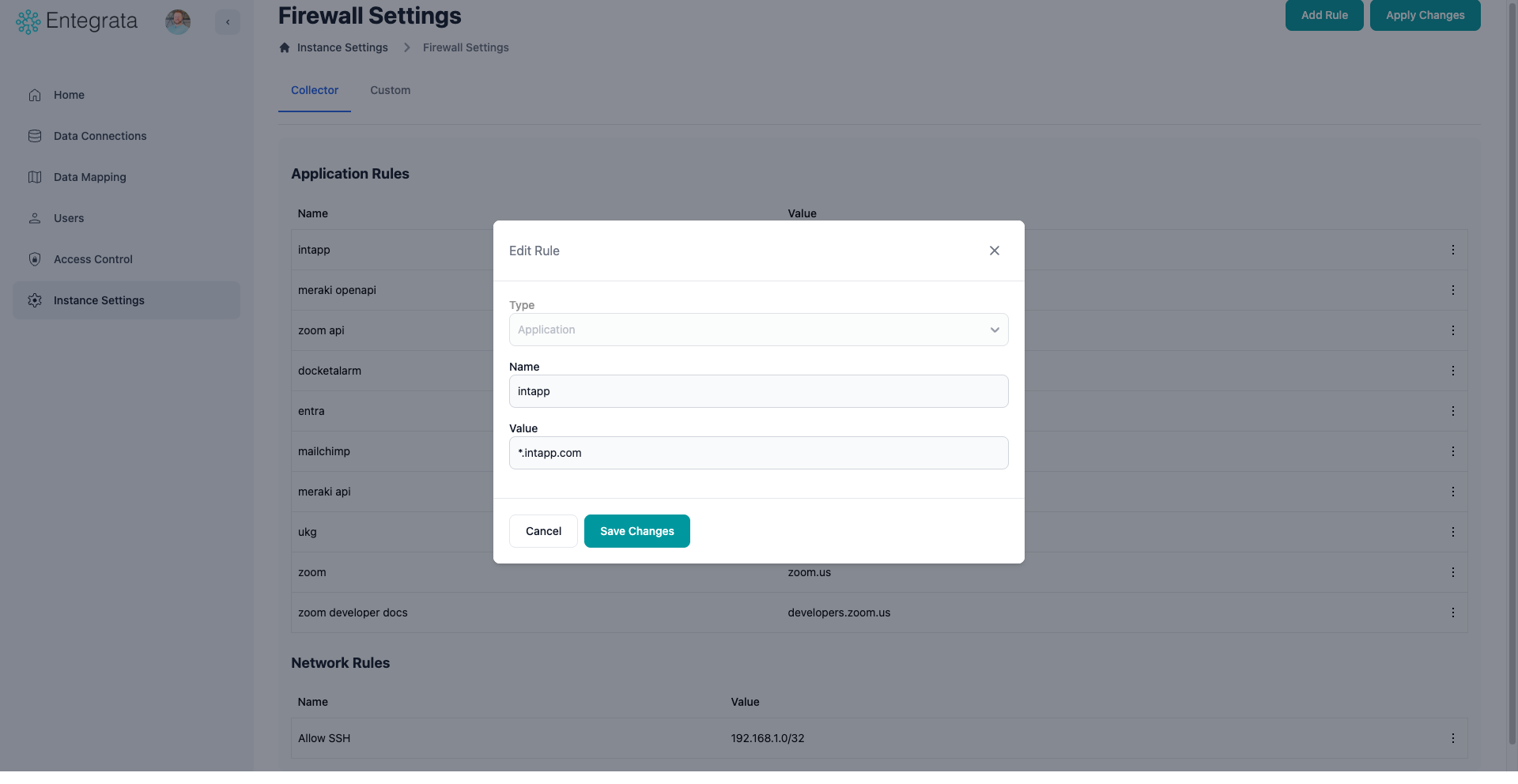

When to Edit Rules
Common scenarios requiring rule edits:- Domain migration: Service moves to new domain
- IP address change: On-premises system gets new IP
- Scope adjustment: Expand or narrow CIDR range
- Subdomain change: API endpoint URL changes
- Typo correction: Fix incorrectly entered domain or IP
Deleting Firewall Rules
Remove a Rule
Identify Rule to Delete
Navigate to the Collector or Custom tab and locate the rule you want to remove.
Confirm Deletion
A confirmation dialog appears to prevent accidental deletions.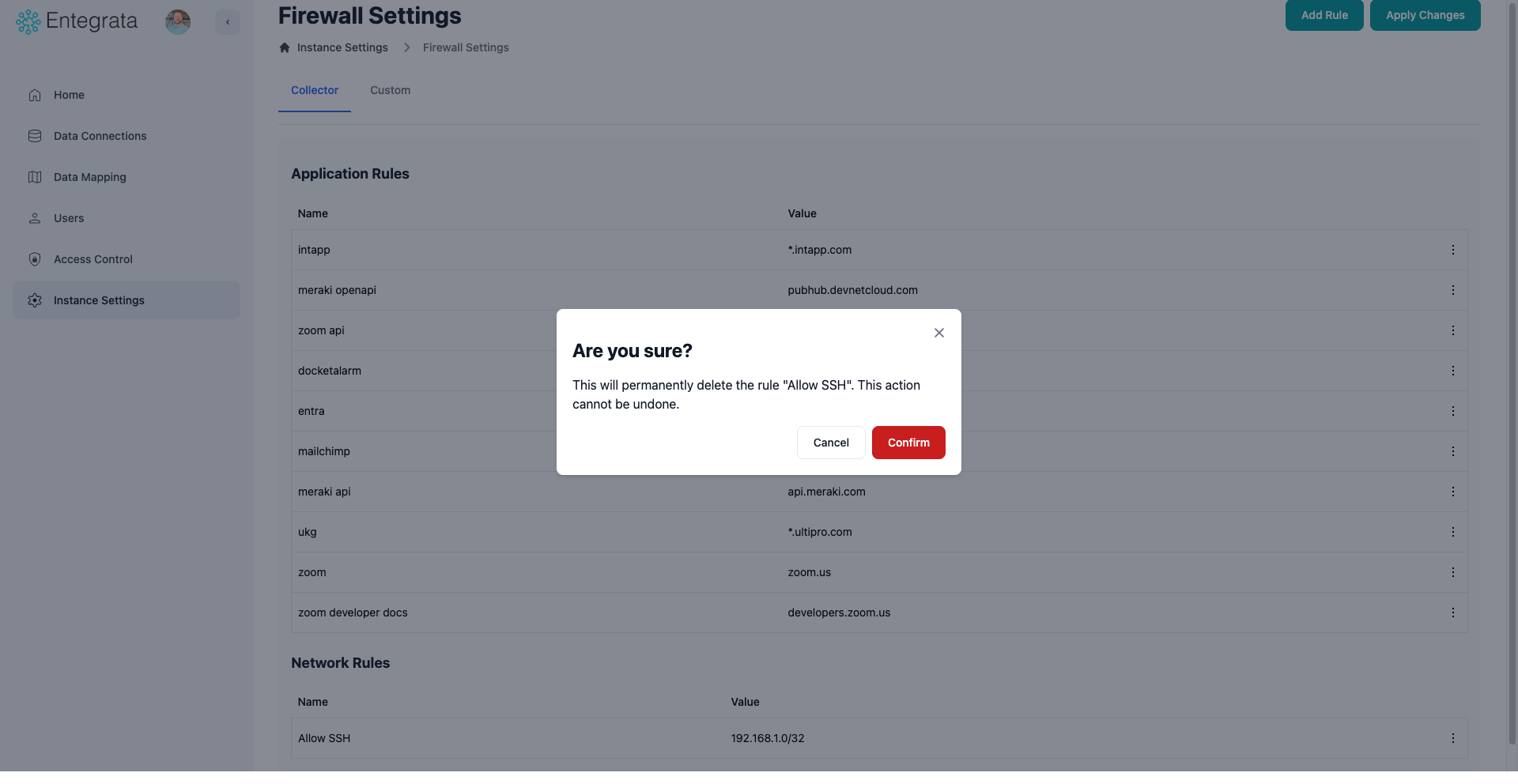

When to Delete Rules
Delete rules when:- Data source retired: No longer collecting from this system
- Integration removed: Service no longer in use
- Duplicate entries: Consolidating overlapping rules
- Security audit: Removing overly permissive rules
- Testing completed: Temporary test rules no longer needed
Applying Firewall Changes
Understanding the Two-Step Process
Firewall rule management uses a save-then-apply workflow:Make Changes
Add, edit, or delete rules as needed. All changes are saved to your configuration immediately.
Review Changes
Changes are staged but not yet deployed to your infrastructure. Your instance continues using the previous firewall configuration.
You can make multiple changes (add several rules, edit others, delete some) before applying. All changes will be deployed together.
Infrastructure Update
The system triggers an infrastructure update:
- Status changes to Transitioning
- A loading screen displays progress showing “Infrastructure is transitioning”
- System polls for completion every 30 seconds
- Changes are deployed via Pulumi Infrastructure as Code
Why the Two-Step Process?
This design provides several benefits:Safety: Review all changes before deploying to productionEfficiency: Batch multiple rule changes into a single infrastructure updateFlexibility: Experiment with rules without immediately affecting infrastructureTransparency: Clear separation between configuration and deployment
During Transition State
While your instance is in Transitioning state:- ✅ Existing firewall rules remain active
- ✅ Data collection continues normally
- ❌ Cannot make additional firewall changes
- ❌ Cannot modify other instance settings
- ❌ Cannot apply new changes until transition completes
Firewall infrastructure transitions typically take 5-15 minutes depending on the complexity of changes being deployed.
Common Firewall Configurations
Example: Whitelist Azure Services
To allow your instance to access Azure-specific services beyond system defaults:Example: Allow Specific On-Premises IPs
For hybrid cloud scenarios with on-premises data sources:Example: SaaS Platform Integration
For collecting data from common SaaS platforms:Example: Restrictive Configuration
For high-security environments requiring minimal access:- Approach
- Sample Rules
- Add specific rules only as collectors require them
- Use exact FQDNs instead of wildcards
- Use /32 CIDR for individual IPs, not ranges
- Regularly audit and remove unused rules
Troubleshooting
Common Issues and Solutions
Collector fails after adding firewall rule
Collector fails after adding firewall rule
Symptoms: Collector reports connection failures despite rule being addedPossible causes:
- Changes not yet applied (still in staging)
- System still in Transitioning state
- Incorrect FQDN or IP in rule
- Rule added to wrong category
- Verify you clicked Apply Changes
- Wait for Transitioning state to complete
- Double-check rule value matches collector configuration
- Ensure rule uses correct type (FQDN vs IP)
- Check collector logs for actual connection target
Cannot add new firewall rule
Cannot add new firewall rule
Symptoms: Add Rule button is disabled or form won’t submitPossible causes:
- System in Transitioning state
- Validation error in rule input
- Network connection issue
- Wait for any infrastructure transitions to complete
- Review validation messages in the form
- Ensure FQDN/IP format is correct
- Try refreshing the page
- Check browser console for errors
Wildcard rule doesn't work as expected
Wildcard rule doesn't work as expected
Symptoms: Connection fails despite wildcard rule that should matchPossible causes:
- Wildcard only covers one subdomain level
- Service uses different domain than expected
- Rule not yet applied to infrastructure
- Remember
*.example.commatchesapi.example.combut NOTapi.sub.example.com - For nested subdomains, add multiple rules or use exact domains
- Verify the rule has been applied (not just saved)
- Check service documentation for actual endpoints used
Changes stuck in Transitioning state
Changes stuck in Transitioning state
Symptoms: Apply Changes triggered but state doesn’t return to IdlePossible causes:
- Azure infrastructure provisioning delay
- Backend service issue
- Network connectivity problem
- Wait at least 15-20 minutes for infrastructure updates
- Refresh the page to ensure you’re seeing current status
- Check Azure portal for any alerts in your subscription
- If persists beyond 30 minutes, contact Entegrata support
The system polls status every 30 seconds during transitions. If the loading screen stops updating, try refreshing your browser.
Deleted rule still allowing traffic
Deleted rule still allowing traffic
Symptoms: Traffic continues to flow through a deleted rulePossible causes:
- Changes not applied yet (rule still in staging)
- Infrastructure update hasn’t completed
- Cached connections still active
- Ensure you clicked Apply Changes after deletion
- Wait for Transitioning state to complete
- Some connections may remain active for minutes after rule removal
- Verify the rule is actually gone from the rules list
CIDR range too broad error
CIDR range too broad error
Symptoms: Cannot add network rule with desired CIDR rangePossible causes:
- Range exceeds security policy limits
- Attempting to use
/0(all IPs)
- Use more specific CIDR ranges
- Break large ranges into smaller, justified subnets
- Document business justification for broad ranges
- Consider multiple specific rules instead of one broad rule
While technically valid, very broad CIDR ranges like
/8 or /0 may be blocked by policy. Contact your security team if you have a legitimate need for broad ranges.Diagnostic Steps
If you’re experiencing firewall-related issues:Verify Rule Exists
Check the firewall management interface to confirm the rule is present in Collector or Custom categories.
Confirm Changes Applied
Ensure the Apply Changes button has been clicked and the transition completed successfully.
Check Rule Accuracy
Verify the FQDN or IP exactly matches what your service needs to access. Check for typos.
Test Connectivity
Use collector logs or diagnostic tools to verify the connection attempt and see actual failure reasons.
Examine Rule Type
Ensure you’re using the correct rule type (Application for domains, Network for IPs).
Security Best Practices
Rule Management Guidelines
Firewall Security Recommendations
Principle of Least Privilege
- Only allow access to services actively in use
- Use specific FQDNs over wildcards when possible
- Prefer /32 CIDR (single IP) over broad ranges
- Document the purpose of each custom rule
- Review firewall rules quarterly
- Remove rules for retired systems or integrations
- Verify collector rules match active collectors
- Update rules as services migrate or change
- Test rule changes in non-production environments first
- Document why each rule is needed
- Coordinate firewall changes with security team
- Plan changes during maintenance windows
- Set up alerts for failed collector connections
- Review logs for blocked connection attempts
- Track when rules were last modified
- Monitor for unexpected rule additions
Wildcard Usage Guidelines
IP Range Best Practices
When creating network rules with CIDR ranges:Calculate Range Precisely
Calculate Range Precisely
Use a CIDR calculator to ensure your range includes only the intended IPs.Example: If you need IPs
192.168.1.5 through 192.168.1.10 (6 IPs):- ❌ Don’t use:
192.168.1.0/24(256 IPs - too broad) - ✅ Do use:
192.168.1.5/32,192.168.1.6/32, … (individual IPs) - ✅ Or use:
192.168.1.4/29(8 IPs - closest range)
Document IP Assignments
Document IP Assignments
Maintain documentation of what each IP or range is used for:This helps with audits and troubleshooting.
Example Documentation
Plan for Growth
Plan for Growth
If you expect to add more IPs in the future, consider using a slightly broader CIDR range from the start:Scenario: Currently need 2 IPs, expect to grow to 10 IPs in subnet
- Current need:
192.168.1.5/32,192.168.1.6/32 - Better choice:
192.168.1.0/28(16 IPs) - allows for growth